Tl;dr
This is highlights from my one hour presentation at HITB 2015 Conference in Amsterdam. Slides and full whitepaper can be downloaded at HITB website.
This is highlights from my one hour presentation at HITB 2015 Conference in Amsterdam. Slides and full whitepaper can be downloaded at HITB website.
#HITB2015, Amsterdam,28th May, Uncovering Secret Connections Using Network Theory and Custom Honeypots. Looking forward to see you at our talk!
Come and join our presentation, So you think all those attacks are originated from China? Let’s go through a journey of an in-depth investigation of attacks by using custom honeypots. 2nd May, 14:03 #WAHCKon [2], Perth
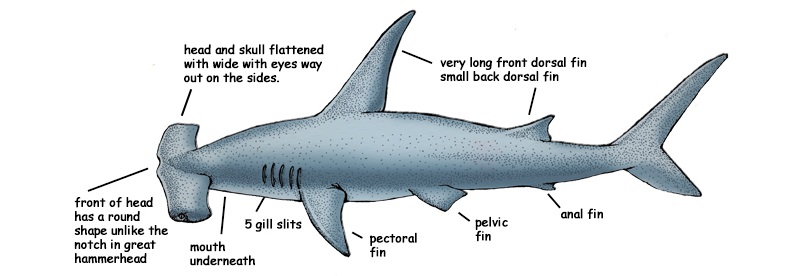
Active defence (or active defense) is relatively a new approach within IT security field. There have been some efforts to define this term. However, the majority of these definitions are incomplete, unspecific, or missing essential attributes of this security approach. Some even mixed up active defence approach with offensive security techniques.
The purpose of this article is to describe key attributes of active defence and highlight what this approach is about and what it is not about.

Honeypot systems have been around for more than a decade. There have been a number of initiatives such as The Honeynet Project or Project Honeypot that have had a great impact on development and adaption of honeypot systems.
However, within enterprises, honeypot systems have not been widely adapted or used. This could be due to difficulty in setting up and managing a honeypot system as well as not knowing their invaluable benefits. The focus of this article is to highlight 5 effective use-cases of a honeypot system for any enterprise.
Thanks to everyone who’s joined our talk at @BsidesLjubljana. We will be also presenting this year at @WAHckon and then @HITBSecConf
Tomorrow (12 March), 3pm, Track 1, come and join our presentation on “Uncovering the secret connections among online attackers using network theory and custom honeypots” at #BsidesLjubliana, http://bsidesljubljana.si/schedule/ https://csa-cee-summit.eu/ #CSA #CEE Summit 2015
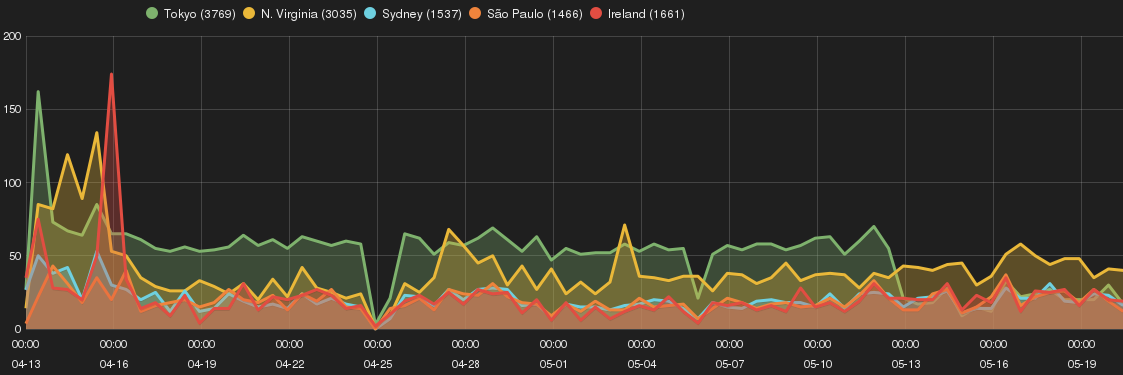
The experiment highlights the correlation among sources and types of attacks across Amazon EC2 geographic zones (or regions) by using Smart Honeypots. The purpose is to identify whether choice of EC2 geographic region has an impact on risk profile of a Cloud-based host.
The research study investigates Secure Shell (SSH) attacks on Amazon EC2 cloud instances across different AWS zones by means of deploying Smart Honeypot (SH). It provides an in-depth analysis of SSH attacks, SSH intruders profile, and attempts to identify their tactics and purposes.
Key observations for this research experiment are as following:
Different variance of ‘old’ php-cgi remote code execution vulnerability (i.e. CVE-2012-1823) was observed across EC2 Smart Honeypot instances. The interesting piece was differences in the attack drop-by files::