Summary
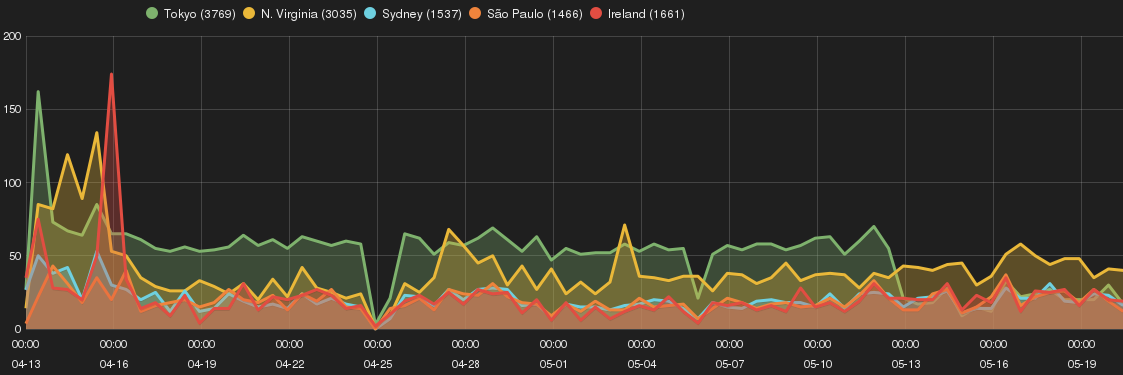
The experiment highlights the correlation among sources and types of attacks across Amazon EC2 geographic zones (or regions) by using Smart Honeypots. The purpose is to identify whether choice of EC2 geographic region has an impact on risk profile of a Cloud-based host.
- With only 6% correlation on source of intrusions, 94% of intruders were unique to each zone.
- The attack profile between zones were completely different. Tokyo zone received significant number of NTP amplification intrusions, where Ireland suffered the most from SNMP scanning and N.Virginia from SSH brute-force attempts.
- Intruders targeting N.Virginia were mainly sourced from Russia and China, whereas Sydney zone received most intrusions from Netherlands.
- Except for DNS amplification intrusions that widely observed on all zones, intruders were only targeted a single zone.
- DNS amplification, SSH brute-forcing, VoIP, SNMP and UPNP scanning had the highest correlation across all zones.
- Ecatel and Firering (NL), OVH (France), Redstation (UK) and VolumeDrive (US) were top non-Chinese providers that allowed for their environment to be used for launching attacks.
- Read our recommendation (on the last page) on how to improve the security of your cloud instance by getting access to our cloud-based custom blacklist service.