Tl;dr
This is highlights from my one hour presentation at HITB 2015 Conference in Amsterdam. Slides and full whitepaper can be downloaded at HITB website.
This is highlights from my one hour presentation at HITB 2015 Conference in Amsterdam. Slides and full whitepaper can be downloaded at HITB website.
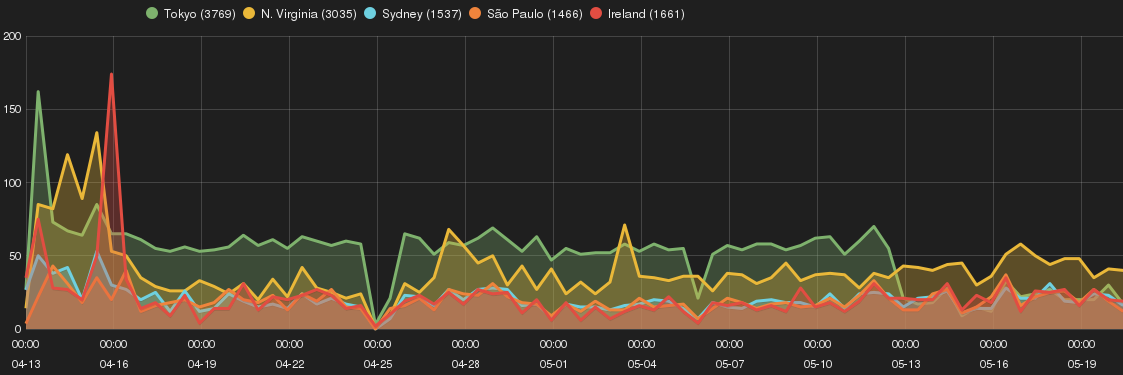
The experiment highlights the correlation among sources and types of attacks across Amazon EC2 geographic zones (or regions) by using Smart Honeypots. The purpose is to identify whether choice of EC2 geographic region has an impact on risk profile of a Cloud-based host.
The research study investigates Secure Shell (SSH) attacks on Amazon EC2 cloud instances across different AWS zones by means of deploying Smart Honeypot (SH). It provides an in-depth analysis of SSH attacks, SSH intruders profile, and attempts to identify their tactics and purposes.
Key observations for this research experiment are as following:
Different variance of ‘old’ php-cgi remote code execution vulnerability (i.e. CVE-2012-1823) was observed across EC2 Smart Honeypot instances. The interesting piece was differences in the attack drop-by files::

It is a jungle out there! If you happen to run a honeypot, you will be amazed by number of intrusions your receive in matter of a few minutes. The issue is even bigger when it comes to servers hosted on cloud. They are constantly being targeted by online adversaries and cyber criminals. The public IP addresses assigned to every cloud instance is from a predefined IP address pool. Therefore, from adversaries perspective it is trivial to identify and target these cloud instances.
We started a journey of experiments and called it Project Amazon EC2 to find out what attacks are received by cloud hosts on a major cloud provider specifically Amazon Web Services (AWS).
We have deployed a number of Smart Honeypots across AWS geographic zone. We make each cloud host to mimic a typical cloud hosted server often used by online business to server a public website.
The observations have been fascinating and we regularly share the results though our blog posts, mailing list and tweets.